Article
The Cyber Insurance Market Needs Rate, but Rate Alone Won’t Solve the SMB Cyber Problem
Why strategic rate deployment combined with active security solutions offers a better path forward for brokers and their clients
Attacks on on-premise VPN appliances exploded in 2025 — based on our claims data, one ransomware group alone drove a 300% surge in Sonicwall incidents between Q2 and Q3. These weren’t typical attacks. Ransom demands more than doubled compared to previous incidents, averaging $958K.
Most concerning, these attacks happened at unprecedented speed: one and a half days on average, with some cases moving from initial intrusion to full encryption in less than one hour.
For the cyber insurance market, this spike in ongoing attacker activity is the new normal — and something carriers must contend with. At-Bay’s claims data reveals ransomware incidents increased 19% year-over-year in 2024, while average severity rose 13%. Financial fraud is also skyrocketing thanks to the use of AI.
The market needs rate to handle the sustained increases in frequency and severity.
At At-Bay we’re taking a measured approach to this challenge – we’re not just going to issue rate blanketly across our entire portfolio. We’re going to focus on the segments that matter the most. I want to share why precision matters in this moment, not just for us, but for the brokers and clients navigating these market dynamics over the coming months.
The Loss Story Is Real, but It’s Not Uniform
As the soft market persists, and cyber attacks increase, it’s clear we need rate — but not all segments are created equal. The rise in ransomware frequency and severity is concentrated among SMBs with revenues between $25M-$250M. These are businesses that are growing rapidly, often without security infrastructure to keep pace with their expansion. They’re adding remote access tools, spinning up new cloud environments, acquiring other companies — all while their security teams (if they have them) struggle to maintain visibility and control.
This isn’t just about company size either. We’re seeing elevated ransomware losses in specific sectors like manufacturing, law firms, healthcare, education, and retail. And there’s a technological through-line in many of these claims. Businesses using remote access tools, particularly on-premise VPNs, are experiencing significantly higher loss activity. According to At-Bay’s 2025 InsurSec Report, remote access tools were the initial entry vector for 80% of our ransomware claims. The tools once believed to be protecting businesses are now their greatest vulnerability.
The threat landscape has fundamentally shifted, even as many in the market continue to price and underwrite based on yesterday’s attack patterns.
Why VPNs Have Become Ground Zero for Loss
VPNs are risky for three fundamental reasons: they add a front door to a company’s network that attackers can target directly, they’re difficult to configure properly and maintain, and they’ve become magnets for vulnerability discoveries. This complexity creates an enormous attack surface that most companies don’t fully understand how to secure.
The consequences are playing out in real time. As we noted earlier, in July 2025, At-Bay’s Response & Recovery Team saw a 300% surge in Akira ransomware cases, nearly all involving SonicWall. These weren’t typical attacks. Ransom demands more than doubled compared to previous Akira incidents, averaging $958K. Most concerning, these attacks happened at unprecedented speed: one and a half days on average, with some cases moving from initial intrusion to full encryption in less than one hour.
This isn’t an anomaly. It’s the new normal for VPN-related risk as threat actors have industrialized their approach to exploiting these devices, and the volume of newly discovered vulnerabilities continues to accelerate. However, the market narrative right now for insurers is simply, “VPNs are bad, charge more or don’t underwrite them.” That’s too simplistic. All VPNs create heightened risk, but not all VPNs are created equal. What matters is how these tools are managed, how many are in use, and which specific products a company has deployed.
A well-configured, actively monitored VPN presents dramatically different risk than an on-premise Cisco ASA device that hasn’t been patched in six months. Our data shows that companies using certain VPN products — specifically Cisco and Citrix devices — are 6.8X more likely to experience a ransomware attack. On-premise VPNs overall carry 3.7X the risk compared to businesses using a cloud-based VPN or no VPN at all. Companies with multiple VPN products in their stack face even higher frequency.
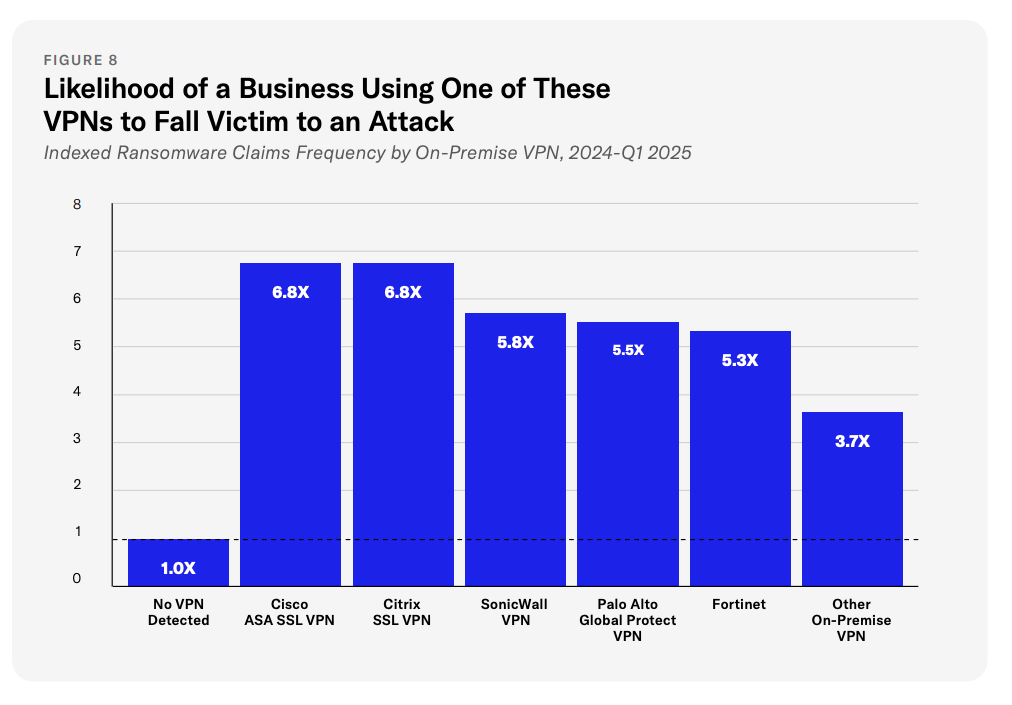
This level of granularity matters because it enables carriers with deep data to be surgical rather than scattershot in how they deploy rate and capacity. Understanding these distinctions is essential for accurate pricing in an environment where VPN-related losses aren’t going away — they’re becoming the dominant ransomware entry vector.
The Secondary Loss Driver: Class Action Lawsuits
There’s another dynamic amplifying severity that deserves attention: a derivative of these ransomware events are increased potential for business interruption and class action lawsuits. Historically, plaintiffs’ firms focused on larger organizations with deeper pockets. That’s changing.
Law firms have become remarkably efficient at monetizing ransomware incidents at smaller companies. When credentials are stolen during a breach — and they almost always are — it creates a straightforward path to allege harm. The sophistication of these legal strategies has improved dramatically, and firms are now going after companies that would have been below their threshold just two years ago.
This means that a ransomware incident that might have resulted in a $200K claim three years ago can now balloon to $500K or even seven figures, once the class action machinery kicks in. It’s an offshoot of the core ransomware problem, but it’s material enough that it needs to factor into how carriers think about exposure.
Deploying Rate With a Scalpel, Not a Sledgehammer
At-Bay is approaching rate with precision and pairing it with solutions that can reduce the need for rate in the first place.
We’re applying rate increases only where our data indicates they’re necessary: accounts with high-risk VPN configurations, in vulnerable sectors, or without adequate security controls. What we are not doing is applying blanket increases across our entire portfolio. Rate is one tool for managing risk, but it’s not necessarily the most effective one — especially when applied indiscriminately.
How Security Plays Into the Rate Conversation
If an insured is running a high-risk on-premise VPN, At-Bay offers a remote access assessment through our in-house security team1. This service is included with our policies, and it often identifies configuration improvements that can be implemented without significant investment. We’re looking for quick wins: enabling multi-factor authentication properly, turning off unnecessary services, improving patch management processes.
If the technology itself is the problem, we’ll help chart a migration path to a SASE solution. Our virtual CISO team can advise on vendor selection and roadmap planning — another service that’s included in At-Bay policies at no additional cost.
For accounts where moving away from a VPN isn’t feasible, we recommend managed detection and response (MDR) solutions2. The data here is unambiguous. During the recent surge in SonicWall-related Akira ransomware attacks, half of the victims who suffered full encryption were already running a top-tier Endpoint Detection and Response (EDR). But insureds with EDR plus 24/7 monitoring — true Managed Detection and Response (MDR) — saw zero encryption events3. The managed component, the human-in-the-loop who’s watching and responding at 1 a.m. on a Saturday, is what makes the difference
Not only does implementing MDR for Endpoint help protect insureds at the point of attack, but we can also eliminate ransomware retentions, remove waiting periods for ransomware events, and guarantee a flat renewal even if they experience a claim4. That’s because our data demonstrates the value of the risk mitigation these solutions provide.
What This Means for Brokers
Given the market softness we’ve seen over the past few years combined with current loss trends, rate is necessary across the market. Pricing pressure is not going away.
The carriers who have invested in building sophisticated risk assessment capabilities can tell you why rate is being applied to a specific account and offer alternatives. And critically, we can bring solutions to the table that can help reduce or eliminate the need for rate increases entirely. An account that looks like it needs 25% rate with a $100K ransomware retention might need 5% rate with a $25K retention if the insured is willing to implement MDR.
The current market needs rate, but it also needs carriers willing to do the harder work of understanding risk at a granular level and partnering with insureds to actually reduce it. That’s the approach that’s going to create stability, not just for carriers, but for the brokers and businesses who depend on cyber insurance being available and sustainable.
1 Access to certain At-Bay Stance offerings are available via the Embedded Security Fee and corresponding Endorsement. Please refer to the policy form for additional information.
2 At-Bay Stance MDR is provided by and available for purchase separately through At-Bay Security, LLC (“At-Bay Security”), a wholly owned subsidiary of At-Bay, Inc. Stance MDR is not required for insurance coverage through At-Bay, and it is not limited to At-Bay policyholders. Similar credits and enhancements available for comparable solutions.
3 Source: At-Bay Security Response & Recovery
4 The availability of this and all coverage enhancements listed in this article will be based on the specific risk profile of the business and subject to qualifying conditions.






